Security has been called the internet of things’ Achilles heel, and with good reason. Even when IoT connections use the most secure wireless networks, data can be vulnerable at both endpoints of a connection. Unlike smartphone data, IoT data doesn’t always start and end its journey with a human who can make decisions about who sees it. Data needs to be secured on the connected device, on servers in the cloud, and at every point in transit.
Even the most mundane data sets can have immense value to thieves when they are aggregated and analyzed. For example, some IoT use cases have used connected soil sensors to support precision agriculture. Data about dirt may not seem valuable to most people, but already a foreign national has been convicted of trying to hack Monsanto and DuPont Pioneer to steal trade secrets related to corn cultivation.
The security challenge is a big one for hardware manufacturers and service providers that specialize in mobile resource management and machine-to-machine connectivity. When designing their solutions, device makers often turn to Gemalto for security solutions. Gemalto’s “secure element” and module secure data on the device, throughout the connection to the cloud, and back to the device.
Gemalto has been setting the standard in security for years as the world’s leading manufacturer of SIM cards and a pioneer in connected device security. From the payment and financial industry, to government-issued ID’s, enterprise security and the IoT, Gemalto’s secure elements, identity authentication and encryption solutions enable its clients to secure digital services for billions of individuals and things.
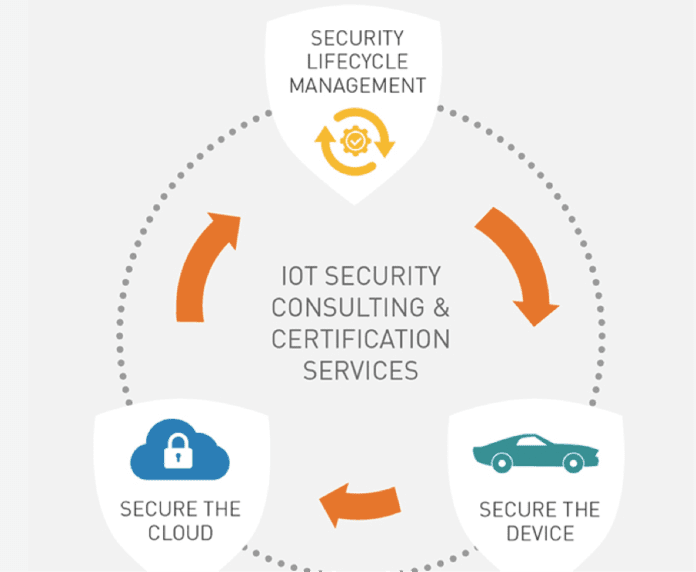
Gemalto’s Juan Carlos Lazcano, VP of M2M for the Americas region, explained that there are three pillars to Gemalto’s IoT solution. First the Cinterion Secure Element, a tamper resistant embedded hardware component, securely connects devices to the network. Second, Gemalto’s enterprise data encryption, cloud security, and licensing enforcement secure the cloud environment and intellectual property. And third, Gemalto’s identity management, software monetization, and encryption key management provide a sustainable security lifecycle management infrastructure.
Extra layer of security
Lazcano said the secure element adds another layer of security to cellular network communications. He compared traditional LTE data transmissions to an envelope that is secure in transit, but open at both its source and its destination. Gemalto’s secure element adds a second envelope inside the first one, so that even when the outer envelope is open the data inside is secure.
“In the absence of end-to-end security, devices and data are vulnerable to attack,” Lazcano said. He said that while the cellular connection from the gateway to the core is secure, security gaps exist between the transmitting device and the gateway modem, and at the server side once the data reaches its destination.
Strong device authentication and credential and key management are critical components in maintaining secure IoT networks. Gemalto’s tamper resistant secure element offers smart card level digital security that ensures strong device authentication. This, combined with Gemalto’s specialized Machine Identification Module (MIM), a ruggedized industrial grade SIM, creates a strong authentication token for cellular connections. As for non-cellular Low Power Wide Area Networks (LPWAN), Gemalto’s Trusted Key Manager allows for credential management for all devices in the field. Lazcano stressed that securing these devices “at every level” was critical in maintaining a sustainable security lifecycle management infrastructure.
Lazcano said that Gemalto’s secure element, secure cloud and security lifecycle management solutions are similar to security technology that Gemalto has successfully deployed with financial, government, and mobile network customers globally for many years. When IoT service providers invest in these solutions, they are able to complement mobile network technology by securing data at the endpoints. This is a point of distinction for IoT service providers when they take their solutions into the marketplace. If security is the IoT’s Achilles heel, Gemalto is offering its customers a solid set of boots.
Join Gemalto’s Panel of Experts at the Enterprise IoT Summit 2017. Explore the architectural foundations and challenges present in a successful IoT deployment. Discuss successful use cases, review crucial global connectivity considerations, and receive hands-on experience with Gemalto’s IoT concept board and prototyping process. Only 20 spots available. Reserve your seat now!