5G is many things, chief among them an exercise in managing complexity. The network is becoming more complex, the way the network is being used is becoming more complex and MEC is another line item on the list of complexities, albeit one with a very direct link to service revenue.
Terry Young, director of service provider and 5G product marketing at A10 Networks, reflected on the work her company has done with operators deploying mobile edge computing infrastructure. There are a common set of decisions that have to be made on the front end, then another set of challenges that have be addressed in execution.
Calling out the link between distributed computing, digital transformation and business success, Young said, “It seems like it’s getting crowded at the edge. Everybody wants to be part of this new ecosystem. For mobile operators, they are having to respond to the traffic demands, the devices, the subscriber applications…and having to manage multiple network transformations,” including MEC. But, “MEC is more than just a technology and more than just an architecture. MEC is a business strategy.”
To effectively implement that strategy, Young laid out some of the key front-end considerations operators need to make:
- What type of services do you want to offer?
- What functions need to be deployed where?
- Do you use existing sites, partner with enterprise and/or cloud providers, or a combination of both?
- What form factor (virtual, physical, container or combination) best fits the strategy?
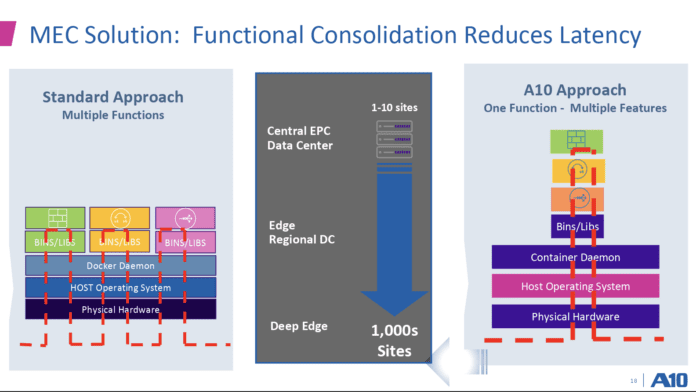
“How they deploy has a direct impact on what services they can offer,” she said. “The closer to the user, the lower the latency and therefore the different types of services.” Once you’ve answered these questions and come up with how MEC supports your business strategy, it’s time to go deploy–a process rife with another set of challenges. Young focused on three recurring hurdles: Space and power constraints, security vulnerabilities, and operational complexity.
To the space and power point, Gi-LAN functions lie firewalls, traffic steering, load balancing, DDoS detection and mitigation, Deep Packet Inspection and more can require multiple physical appliances. As the number of sites increase with the move to the edge, this isn’t scalable. “So operators are really choosing to virtualize those functions,” Young said, and take the next step of functional consolidation via both form factor and software-related efficiencies.
To the security point, the simple explanation is that more equipment in more places equates to an increased attack surface. DDoS attacks are, in particular, a “significant threat to edge services,” Young said. To keep paces with evolving style and strategy of DDoS attacks, each edge location needs its own protection and the monitoring that goes along with it, which runs directly into the operational complexity problem, which runs directly into cost.
Young gave the example of customer SK Telecom, which was an early mover on commercial 5G and has refined its MEC strategy by deploying 12 initial nodes to support service clusters defined by geographic, demographic and usage characteristics. “They’re doing this to more closely align investment resources with revenue opportunity and the requirements of those particular services.”