Security and the connected car seem to be linked on a daily basis in the news the last few weeks. The question regarding hacking of the connected car has gone from if to when. Now the question is what is the best way to protect from these occurrences? This protection is required on two levels – the physical safety of the vehicle and the passengers traveling inside and the security of the private data onboard. Inside Secure has some answers to key concerns related to the connected car and the Internet of Things in general.
Inside Secure provides embedded security solutions to companies requiring mobile security and secure transactions to protect critical assets. These include connected devices, content, services, identity and transactions. Solutions can be delivered via a range of IP, semiconductors, software and associated services.
Over the past few weeks there have been a range of high-profile attacks on the connected car. Most planned as a test; such as the Wired Jeep Cherokee hack that resulted in the recall of 1.4 million vehicles. Quickly followed by the University of California, San Diego hack that cut a Corvette’s brakes via text messaging to the OBD2 dongle used for many fleet tracking and usage-based insurance programs. And then researchers hacked a Tesla, but the good news is Tesla was able to send an OTA fix to keep the problem from happening in real life.
During my discussion with Inside Secure, the connected car was positioned as a “complicated network on wheels” and as a result there are many opportunities to exploit it. To me, this is a great way at looking at the connected car as it evolves into the future and technologies such as Wi-Fi and Ethernet play a greater roll, the opportunities for security breeches will only increase. Today the scenario is following the path of finding an exploit, patching it and then going on to the next exploit. This is a never-ending cycle if it isn’t stopped.
There are two paths to consider in thwarting potential attacks, hardware and software. If hardware is used it needs to be deployed in all systems from the beginning and if there is a problem this requires a recall and retrofit of the impacted hardware. With software the opportunity to identify and address issues on the fly with over-the-air updates is a possibility. 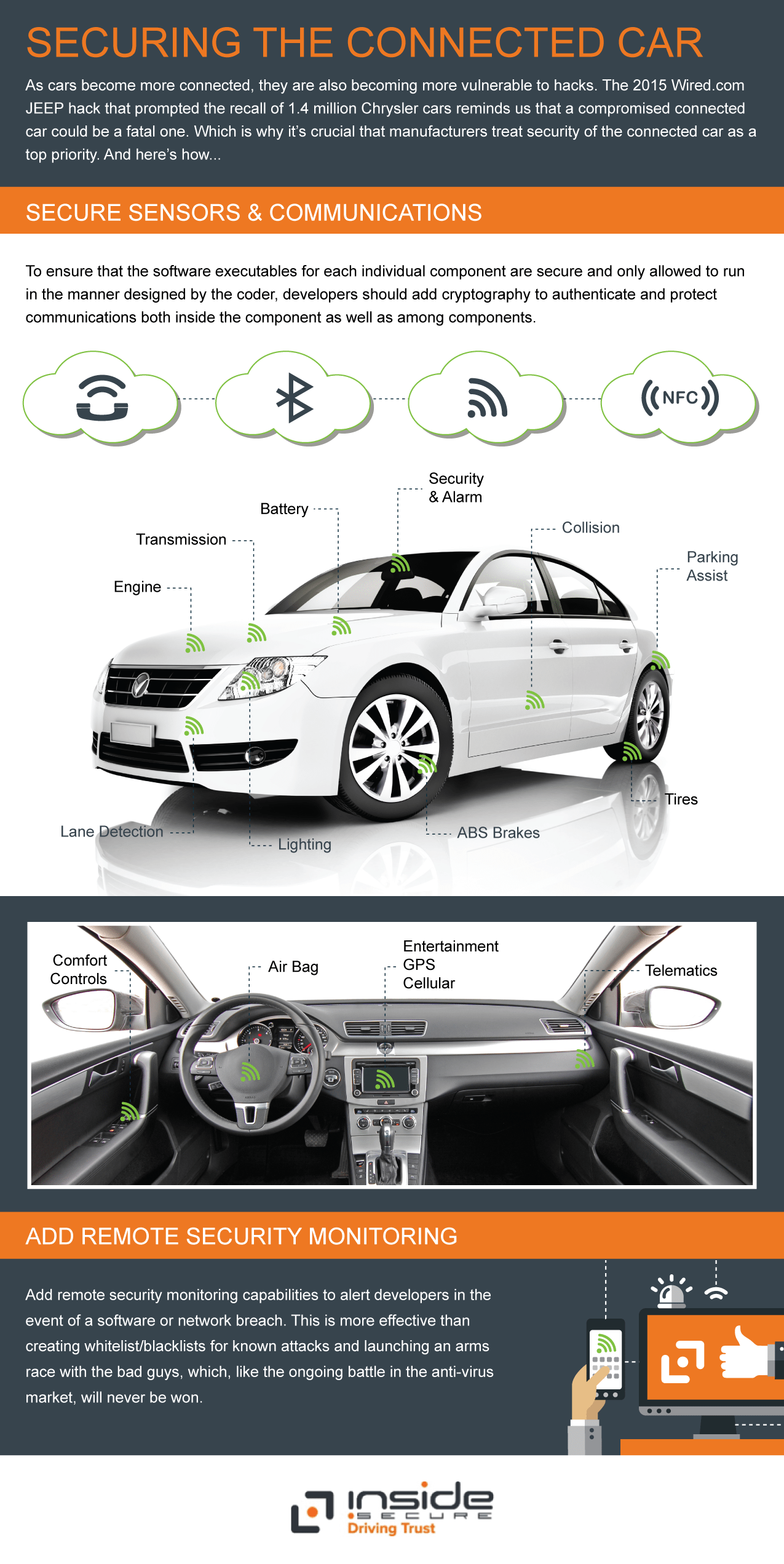
So how are attackers impacting connected cars remotely today? In the example of the Jeep Cherokee attack the infotainment system was exploited in order to gain access to increase the privileges of the hackers for root level access. Once this occurred they could actually change the code controlling the features within the vehicle. Today’s attacks are about the ability to rewrite code.
Earlier this year I attended a session at CeBit with Michael George, a former German anti-espionage agent and author of “Hacked: How Network Attacks Threaten Us All” and he talked about the level of interest of hackers in the connected car would rise once there were ways to monetize this hacking. I asked Andrew McLennan, President, Inside Secure his this thoughts on this topic and he was able to come up with five ways hacking the connected car could be monetized. Recognizing that most real hacking is driven by organized crime, the following topics came to mind:
- Unlock the door and steal your car
- Sell your location information to people wanting to know where you are or maybe where you aren’t (in your home)
- Owner extortion for money – we own your car by controlling it, pay us if you want your car back
- Manufacturer extortion – threatening to take control of cars of a specific manufacturer unless a ransom is paid
- Once connected cars have the ability to purchase and make payments this will be the same scenario as the internet in stealing credit information.
It’s becoming a scary world out there I think.
As vehicle-to-X comes in to play this challenge increases the need to ensure a trusted source at the other side of the communication. One scenario to identify the source is to have a regular ping to the car to basically say ‘yes it’s still a car’ on the other side. Interesting concept.
With IoT the question varies a bit. In general it would be very difficult to monetize an IoT hack at the end user level. Although you could open someone’s house or lock the resident out for an extortion payment to enter again, what is more possible is to ruin a brand. Say to take control of all of the connected appliances of a major appliance brand and make them perform inadequately unless they make a ransom payment. This would be a tough scenario to come back from as the trust of the customer is lost.
Like what you read? Follow me on twitter!

